Within the era of electronic digital interaction, personal privacy is the central concern, and if you are using untrustworthy programs, your privacy reaches danger. You could have learned about Privnote, however, if you haven’t, it is about time to know about it. Privnote is definitely an on-line instrument that offers protect and individual conversation methods, making it different from other systems. With Privnote, personal conversation is now more achievable, more secure, and successful than before.
1. What is Privnote?
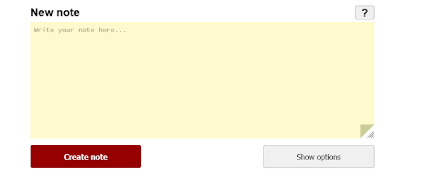
privnot (привнот) is undoubtedly an on the internet tool that allows you to build a safe note and reveal private information like a pass word, magic formula information, personal information, or other exclusive information. Privnote makes use of end-to-stop file encryption, which implies your meaning is just noticeable to the receiver of the email, and no person can entry it, not the Privnote team. Moreover, every one of the messages vanish following simply being study through the receiver, producing your data secure and untraceable.
2. How Privnote operates?
Privnote offers a consumer-friendly program to generate and share the message. You simply have to compose the content, and Privnote produces a unique weblink, which can be shareable. Anytime the receiver of the email click throughs the hyperlink, the content can look for only one time, and therefore the concept will disappear immediately. Although Privnote has an effortless-to-use graphical user interface, it makes use of strong encryption algorithms to secure data.
3. Privnote or. Other Platforms:
In terms of secure connection, several tools offer encryption. However, you will find restrictions or in question level of privacy guidelines on these kinds of platforms. Unlike other programs, Privnote offers conclusion-to-stop encryption, meaning that not any other intermediaries can accessibility the message. Moreover, Privnote’s communications personal-destruct following getting read through, rendering it be noticeable when compared with other messaging software. In addition, you don’t have to join up to utilize this platform, making it simpler to talk anonymously.
4. Use Situations for Privnote:
Privnote can be used in several cases, from revealing passwords with co-staff to sending confidential records for the financial institution. Here are some use instances when Privnote might be beneficial.
– Co-workers can discuss passwords and vulnerable organization documents via Privnote in order to save themselves from hacks and details breaches.
– Lawyers can connect significant paperwork or buyer information with other attorneys, judges, along with the government.
– Medical professionals may use Privnote to share health-related files or sensitive personal information between other healthcare professionals.
– Newspaper writers can depend on Privnote’s self-destruct attribute to talk together with the resources anonymously.
5. How to use Privnote:
Privnote is incredibly simple to use. Right here is how to use Privnote.
– Proceed to the Privnote web site.
– Compose your message inside the meaning container.
– Click the “produce be aware” option.
– Copy the URL website link and reveal it with your beneficiary.
– The recipient will get your message as soon as and this will disappear altogether immediately.
To put it briefly:
Privnote is surely an on the internet instrument which includes transformed the private conversation sector. Its personal-destruct attribute makes sure that your personal details remains secure and untraceable. Privnote is reliable by men and women throughout the world, and its convenience, as well as its solid online privacy policy, can make it the best choice in relation to protect and exclusive communication. In the event you haven’t attempted Privnote nevertheless, test it now and safeguard your information from possible cyber hazards.